The emergence of reliable, low-power, low-cost ‘Internet-of-Things’ (IoT) devices has made it economical to deploy advanced Building Management Systems (BMS) into small to medium - sized buildings, but the relative simplicity of those devices (basic sensors, actuators and communications stacks) could expose those buildings to the threat of cyber - attack, with potentially catastrophic consequences.
An integrated BMS monitors, manages and controls the critical systems within a building - HVAC, lighting, security, fire alarms, access control and more; a sophisticated attack could disrupt, disable or damage these vital support systems.
Deployment of these systems is growing rapidly; according to Gartner around 45% of the 1.1 billion connected things in 2015 were devices in smart buildings and homes and this total is set to explode to around 21 billion devices in a global smart building market estimated to be worth $36bn by 2020.
However, the potential exposure to cybersecurity risks created by these systems appears to be largely ignored; a recent survey of BMS operators suggests that only 29% had taken or were planning to take action to improve their cybersecurity measures.
This may be because these devices typically fall outside the scope of traditional IT systems, requiring specialist knowledge and expertise to manage and protect them effectively. Without such protection hackers could gain access to the BMS, with potentially disastrous consequences.
Whilst some exploits may result in little more than inconvenience (switching off lights or air - conditioning systems), concerted, malicious attacks are already happening – in one recent example the electronic door lock system in an Austrian hotel was over - ridden until a ransom was paid.
With access to the BMS it would be possible to switch off temperature control in computer server rooms whilst simultaneously making the temperature sensors report as normal, quickly leading to over - heating and damage to the servers.
The nature of the problem
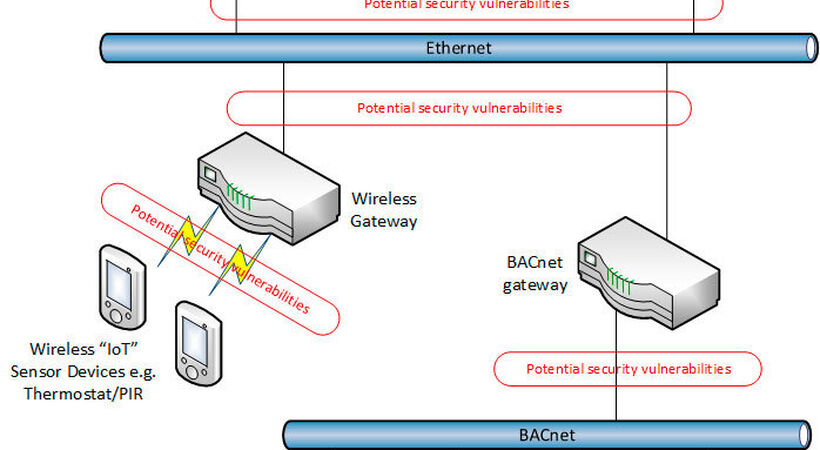
Different types of vulnerability exist in the smart building ecosystem. These range from local issues at device and sensor level up through controllers and gateways to network and application level problems that can affect entire buildings and beyond.
Traditional BMS manufacturers tend to regard their systems as existing in isolation, or on private networks, leading them to place less emphasis on security. Unfortunately, the need for remote control and monitoring inevitably leads to devices being connected to a public network, with all the risks that this entails.
In addition, incompatible devices and standards from different manufacturers increase the challenges of securing these systems.
The answer is to take more of a holistic approach to security, covering both physical and virtual aspects. There is no point in locking the front door to a building then leaving the backdoor to your network wide open!
This may require engaging with specialists who are more familiar with embedded systems, especially IoT device, security. Traditional IT specialists will be familiar with network and application security, and BMS specialists can design and operate smart systems, but the emergence of smart buildings with highly - integrated systems requires a new breed of expert who can identify the complex, rapidly evolving risks and create solutions to mitigate them.
An inconvenient truth
At the most basic level, normal IT security rules need to be applied to the BMS domain. These are straightforward and commonplace in IT today:
- Password security control and re-use rules enforced
- Network IP addresses restricted and all wireless networks secured and encrypted.
- Remote access controlled via address whitelisting and Virtual Private Networks (VPNs) using two - factor authentication
- Software kept up to date and security vulnerabilities patched as soon as updates are available.
- Penetration testing used to establish potential security loopholes.
It is also important to recognise that while the IT security measures are valuable they may not be applicable to all elements of building control systems. Typically the IoT devices (controllers and sensors) used in a BMS have limited processing power and memory capacity, and often are connected via a limited bandwidth network, such as BACnet. Although the BACnet protocol does have provision for security measures, these are frequently not implemented due to their complexity and the limited processing power of these IoT devices.
This makes it difficult to apply conventional IT security rules, so more often physical security measures are applied in areas where BMS equipment is located or where there are BMS network cable runs. However, these network cables may run over extended distances, making them expensive to secure, and it only takes one exposed section of cable to allow access to a determined hacker.
To mitigate these risks research projects are looking to create much more sophisticated (and therefore possibly more expensive) smart building systems. One example is the European project BRESAER, which is developing a Building Energy Management System (BEMS) designed to manage the different functions of a smart system, using energy more efficiently. The system hopes to create a 10% saving on energy used. All information in the BEMS is communicated via a private internal network to restrict external access, although this will clearly also require additional security measures if remote monitoring and control is required.
Systems such as these would be difficult and expensive to retro-fit to existing buildings, so other initiatives, such as the Cisco - led aSSURE project, have demonstrated that low - cost devices can be retro-fitted to secure existing BMS. Localised security measures and data encryption will remove the need for entire cable runs to be secured, yielding greater savings.
Although it’s early days for these proof-of-concept demonstrations, they clearly show a path ahead that could mean the BMS in small to medium - sized buildings can be secured at acceptable cost, and that larger buildings can be retro-fitted, cost-effectively.